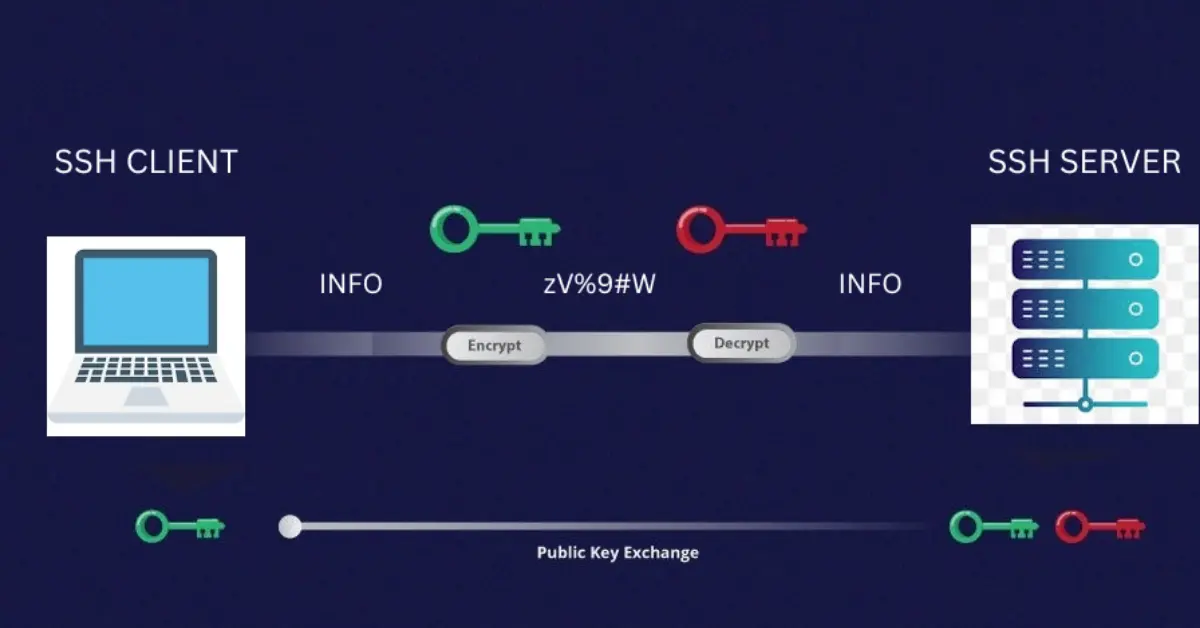
In the realm of Linux server administration, ensuring the security of your systems is paramount. One of the critical components of safeguarding your server is securing the SSH (Secure Shell) access, a fundamental tool for remote administration. As the gateway to your server, SSH demands extra attention to prevent unauthorized access and potential security breaches. In this blog, we’ll explore essential SSH security tips to fortify your Linux server and create a robust SSH shield.
Table of Contents:
- Strong Passwords and Usernames: The First Line of Defense
- Key-based Authentication: Fortify Your Fortress
- Implement fail2ban for Intelligent Threat Prevention:
- Keep Software Updated: Patching the Holes
- Change Default SSH Port: Deter Unwanted Attention
- Ensure Blank Passwords Aren’t a Vulnerability
- Configure SSHD: Fine-tune Security Settings
- Two-Factor Authentication (2FA): Double Down on Security
- IP Whitelisting: Restrict Access
- Regular Audits: Continuous Vigilance
- Educate Your Team: The Human Firewall
- Conclusion
- FAQs
Also See: Automate SSH Connections Using Bash Script
1. Strong Passwords and Usernames: The First Line of Defense
The simplest but often overlooked aspect of SSH security is having strong, unique passwords and usernames. Avoid default usernames, opt for complex passwords, and consider using a password manager to generate and store them securely.
2. Key-based Authentication: Fortify Your Fortress
Key-based authentication provides a more secure alternative to passwords. Generate SSH key pairs on your local machine and securely transfer the public key to your server. Disable password authentication to strengthen your server’s defense against brute-force attacks.
3. Implement fail2ban for Intelligent Threat Prevention:
An initial step, especially for servers, is to install fail2ban. This tool acts as a shield against malicious and brute-force login attacks and extends its protective measures to other networking protocols like HTTP, SSH, and FTP.
With fail2ban, you create “jails” – configurations that dictate system responses to specific events, such as a failed SSH login attempt. Configuration files, usually named jail.local, reside in /etc/fail2ban/ and look somewhat like this:
[sshd]
enabled = true
port = ssh
filter = sshd
logpath = /var/log/auth.log
maxretry = 3
findtime = 300
bantime = 28800
ignoreip = 127.0.0.1
For Debian-based systems, install fail2ban with:
sudo apt-get install fail2ban -yFor Fedora-based systems:
sudo dnf install fail2ban -y4. Keep Software Updated: Patching the Holes
Regularly updating your server’s software, including the SSH daemon, is crucial. Updates often contain security patches that address vulnerabilities. Set up automatic updates or implement a routine to ensure your system is running the latest, most secure versions.
5. Change Default SSH Port: Deter Unwanted Attention
Changing the default SSH port from 22 to a non-standard port won’t make your server impervious, but it can help deter automated scans and reduce the likelihood of random attacks. This adds an extra layer of security by making it less predictable for potential intruders.
6. Ensure Blank Passwords Aren’t a Vulnerability:
While the chance of having users with blank passwords is low, it’s better to be safe than sorry. Open /etc/ssh/sshd_config and find the line #PermitEmptyPasswords no. Change it to:
PermitEmptyPasswords noSave and close the file, then restart SSH.
7. Configure SSHD: Fine-tune Security Settings
The SSH daemon (sshd) comes with various configuration options. Modify the SSHD configuration file to enforce stricter security measures. Disable root login, limit user access, and implement other security-related settings based on your specific requirements.
8. Two-Factor Authentication (2FA): Double Down on Security
Implementing Two-Factor Authentication adds an extra layer of protection by requiring a second form of verification in addition to passwords or key-based authentication. This could be a time-sensitive code generated by a mobile app or sent via SMS.
9. IP Whitelisting: Restrict Access
Limit SSH access to specific IP addresses or IP ranges by configuring IP whitelisting. This ensures that only trusted machines can connect to your server via SSH, minimizing the potential attack surface.
10. Regular Audits: Continuous Vigilance
Regularly audit your server’s SSH access logs to identify any unusual activity. Investigate unexpected login attempts or access patterns and take immediate action if any suspicious activity is detected.
11. Educate Your Team: The Human Firewall
Lastly, educate your team or any users with SSH access about security best practices. Make them aware of the importance of strong authentication, secure key management, and the potential risks associated with improper SSH usage.
Conclusion
By implementing these essential SSH security tips, you can create a formidable shield around your Linux server. Remember, the key to a secure system is a combination of robust technical measures and a security-conscious user base. Stay vigilant, stay secure!
FAQs
1. What is fail2ban, and how does it enhance SSH security?
Fail2ban is a security tool that protects against malicious login attempts by monitoring various protocols, including SSH. It works by dynamically modifying firewall rules to ban IP addresses that exhibit suspicious behavior, such as repeated failed login attempts.
2. Can changing the default SSH port prevent all attacks?
While changing the default SSH port adds an extra layer of security, it doesn’t make your server immune to all attacks. It’s part of a defense-in-depth strategy, and it’s crucial to combine it with other security measures for comprehensive protection.
3. How does restricting SSH access to specific IP addresses enhance security?
Restricting SSH access to specific IP addresses limits potential entry points, reducing the attack surface. This is particularly useful for environments where only certain users or systems require SSH access, enhancing overall security.
4. What should I do if I get locked out due to fail2ban?
If fail2ban blocks your IP address, you can access your server through a different IP or physically, if possible. Alternatively, you can log in via console or another secure method and adjust fail2ban settings to unban your IP.
5. Is it possible to use both password and SSH key authentication simultaneously?
Yes, it’s possible to enable both password and SSH key authentication for added security. This way, even if one authentication method is compromised, the other layer remains intact, providing a more robust defense against unauthorized access.
6. Are there any tools to audit SSH configurations for security vulnerabilities?
Yes, tools like ssh-audit can be used to audit SSH configurations for security vulnerabilities. These tools analyze the configuration and provide recommendations to improve security based on best practices.
7. How often should I review and update my SSH security measures?
Regularly reviewing and updating your SSH security measures is essential. It’s advisable to conduct security audits periodically, especially after significant system changes or updates, to ensure ongoing protection against emerging threats.